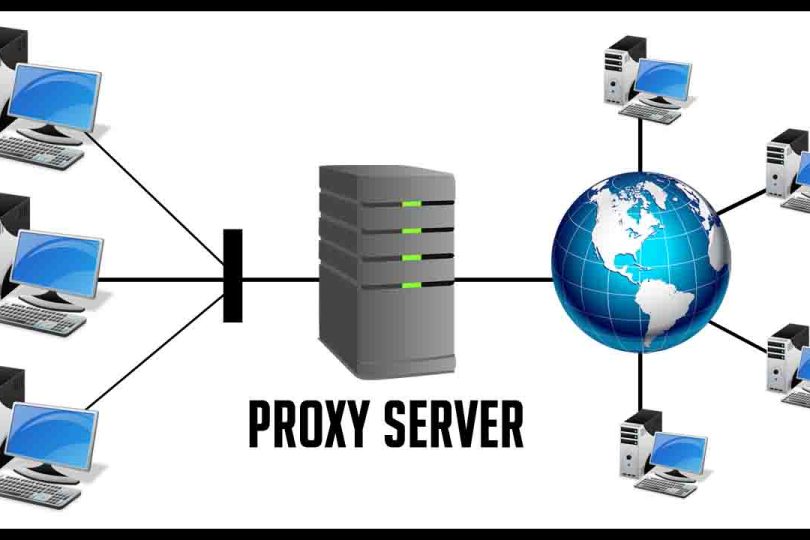
When a user makes a request, a proxy server acts as a go-between to get the requested information from the server. In order for a user to access the websites they are interested in, a server must first be established.
In its most basic form, an IP-assigned computer is what makes up a proxy server. It is the proxy server’s job to evaluate the user’s request before completing it, rather than the user directly connecting to the desired website. A proxy is an additional security, privacy, and structure layer that can be added to an encapsulation request in order to make it simpler or manageable. It is possible to conceal the requester’s actual identity from the recourse server using a proxy server.
Requests are received, evaluated, sent, and forwarded by hardware proxies, which sit between your network and the internet. It is common practice for providers or the cloud to host software proxies. Some software proxies can be installed for free, while others require payment. Paid proxies can meet the needs of businesses. Do you want proxies that allow an unlimited amount of connections and bandwidth? Your search ends here. Privateproxy offers reliable proxy packages.
Table of Contents
Why do people use them?
You can set up proxies to act as web filters or firewalls to help keep malware at bay; they add another degree of protection for your computer.
In conjunction with email security software or a secure web gateway, this feature allows for more stringent filtering of traffic based on the security level and the capabilities of your computer or network.
A person may conceal their location or use a proxy for other private purposes. Business organizations can configure them to:
- Strengthen safety measures
- Boost the security of workers’ online activities
- Keep computer programs from crashing by balancing internet traffic
- Oversee the process by which workers gain access to the workplace.
- Minimize the amount of data that can be transmitted over a specific path by utilizing caching or traffic compression techniques.
You can also use proxies for:
- Media screening
- Decryption of Secure Data
- Overcoming filters
- Spying and logging
- Speeding up operations (by using a caching proxy)
- Translation
- Fixing problems
- Ads that are tailored to specific geographic areas
- Resources that span several subjects
Types of Proxy servers
Forward proxy
It is possible to send data to groups of users on an internal network using forward proxies. In response to a request, the proxy server checks the information and determines whether or not to establish a connection.
Public proxy
Everyone can use public proxies; they conceal their users’ identities by giving them their IP address. Even though this proxy is inexpensive and easy to use, it increases the likelihood of data breaches for its users.
Shared proxy
Several users can connect to this proxy at once because it assigns each user a shared IP address.
Residential proxy
This proxy assigns the user an IP address that can be associated with a particular hardware device that evaluates and redirects all requests.
Anonymous proxy
Anonymous proxy servers evaluate a user’s request while masking their identity in order to cover their online activities.
High anonymity proxy
This proxy goes above and beyond the standard anonymous proxy by further masking the user’s identity. The user’s data is erased by the proxy before it tries to access the desired website.
Transparent proxy
By using a transparent proxy, one can remain undetected by the people it is used to conceal. Employers that want to use proxies but don’t want their employees to know about it can benefit from this kind of proxy. One type of security risk that transparent proxies are more likely to experience is a SYN flood DOS attack.
Distorting proxy
For the purpose of concealing their identity from the intended website, distorting proxies alter their IP address. Those who prefer to remain anonymous online will find this to be a suitable solution.
Data centre proxy
In order to evaluate and redirect the user’s requests, a proxy server can be physically located in a data center. By way of a data centre, it is not linked to any particular internet server but rather to an independent organisation.
Rotating proxy
With a rotating proxy, each user is assigned a unique IP address, separate from the one used by the device that was previously connected.
Reverse Proxy
Rather than being physically located “in front” of end users, a reverse proxy evaluates and redirects browser requests to web servers. A proxy server sits at the edge of a server’s network, receiving requests from users. It then forwards those requests to the original server, where they receive replies.
SSL proxy
An SSL proxy adds an extra layer of security by encrypting all data sent and received. An organization’s security is better served by having these proxies in place.
TOR proxy
This proxy hides the user’s IP address by routing their data through a network that is present all over the world. Multiple layers of encryption are used to further protect the privacy of data. Once the data reaches its destination, each layer is decrypted to reveal the original data.
I2P proxy
Akin to the TOR proxy, but with improved capabilities.
Suffix proxy
However, this proxy does not offer much privacy as it appends the proxy’s name to the URL of the requested content. It is used to bypass web filters.
There’s certainly a great deal to learn about this subject.
I like all the points you made.
Wow, incredible blog layout! How long have you
been blogging for? you made blogging look easy.
The overall look of your website is excellent, as well as the content!
Hi there! Do you know if they make any plugins to protect against hackers?
I’m kinda paranoid about losing everything I’ve worked
hard on. Any suggestions?
You actually make it seem so easy with your presentation but I find this topic to be really something
that I think I would never understand. It seems too complicated and
very broad for me. I am looking forward for your next post,
I will try to get the hang of it!
mail order pharmacy india http://indiaph24.store/# indian pharmacies safe
india pharmacy